
Crytek is a well-known German game developer and publisher most noted for its Crysis franchise. Earlier this month, Crytek confirmed that its encrypted systems containing customers’ personal information were breached by a ransomware group — Egregor — which was later leaked on the dark web. First reported by BleepingComputer, the company sent out letters to the victims of the data theft in which it acknowledges the ransomware attack that happened in October 2020. The letter was shared with BleepingComputer by one of the individuals impacted by the encryption breach.
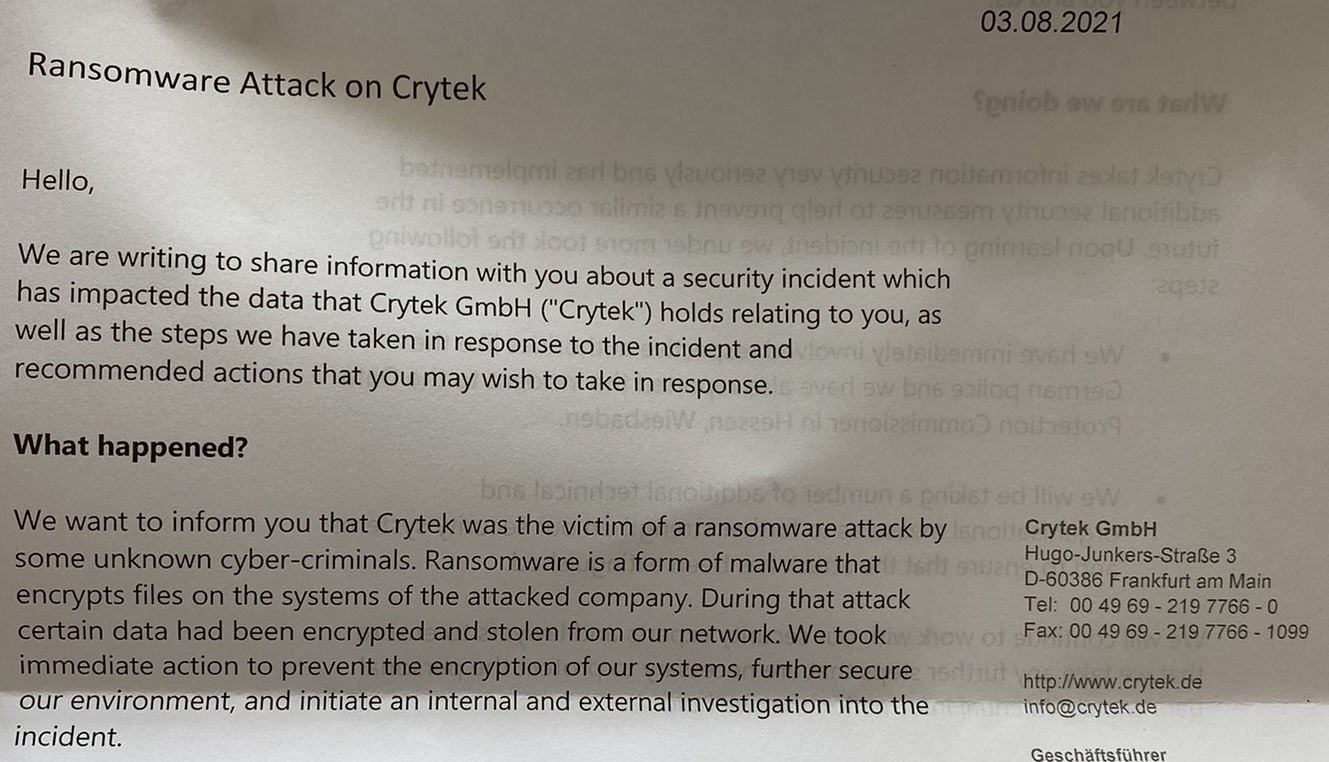
The letter sent out by Crytek to the impacted individuals reads, “We want to inform you that Crytek was the victim of a ransomware attack by some unknown cyber-criminals. Ransomware is a form of malware that encrypts files on the systems of the attacked company. During that attack certain data had been encrypted and stolen from our network. We took immediate action to prevent the encryption of our systems, further secure our environment, and initiate an internal and external investigation into the incident.”

Crytek tried to downplay the data theft by reassuring its customers by saying that the website itself was “difficult to identify” and that in their assessment, only a few individuals would’ve taken note of it. In addition to this, the company also wrote that considering the size of the leaked information, it would’ve taken too long to download it anyway, which would probably have been a struggle for individuals that wanted to get a hold of the data.
Crytek further reassured its customers by telling them that those who did try to download the leaked data were likely thrown off by the “huge risk” of malware embedded in the stolen files that would compromise their systems. It seems like Crytek wants to convince its customers that have little to no knowledge about computers or encryption, Anyone that understands how malware works would know that anyone that wants to get a hold of the leaked information would likely use a virtual machine to download it.
Additionally, those that do steal information and data from companies like Crytek are likely going to sell or share it with other cybercriminals. Crytek is trying to make it seem like the data theft that happened months ago was nothing serious and while that does make sense from a business standpoint, transparency towards customers is absolutely necessary. “While we are not aware of the misuse of any information potentially impacted, we are providing this notice as a part of our precautions,” Crytek wrote in the letter.
In October 2020, familiar sources reported that Crytek had been attacked by a ransomware group that goes by the name “Egregor”. However, no details about how many encrypted systems were breached were provided. The only thing that we knew for certain was that the stolen files had been renamed to include the “.CRYTEK” extension. The stolen data leaked by Egregor on their website comprised of files related to WarFace, the cancelled Arena of Fate MOBA game, and documents that included information about their network operations.
So far, Egregor has also attacked many renowned organisations and companies around the world, such as Barnes and Noble, Kmart, Cencosud, Randstad, and Vancouver’s TransLink metro system. In February, many members of the Egregor ransomware group were arrested in Ukraine during a shared operation between the French and Ukrainian authorities. The ransomware group was arrested after the French law enforcement could trace the ransom transactions back to Ukraine. The arrested members are considered to be associates of Egregor whose responsibility was to hack into security networks and deploy the ransomware attack.
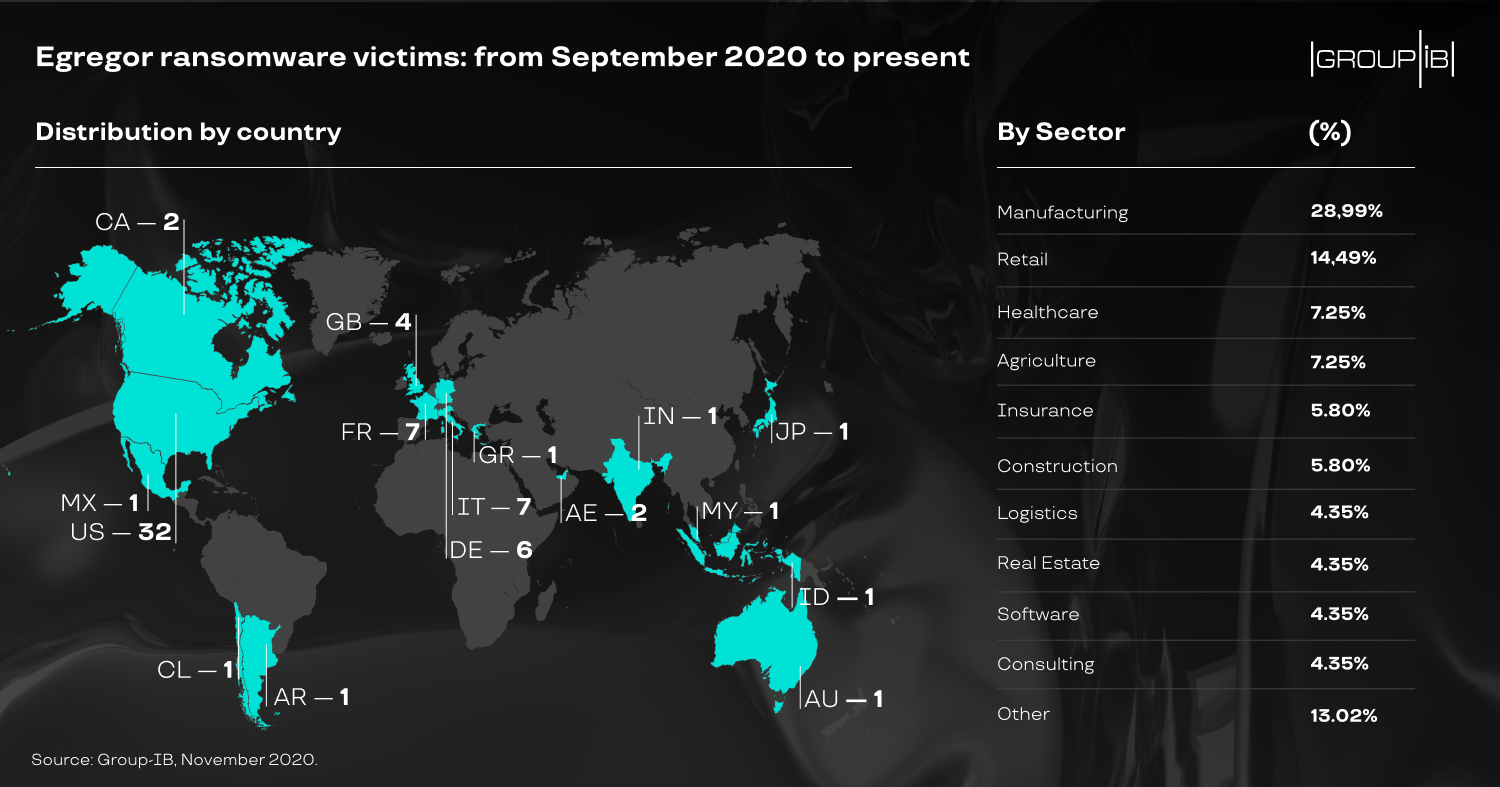
In January, the FBI released an official notification that warned companies and individuals about the security risk that Egregor poses, saying that “the FBI does not encourage paying a ransom to criminal actors”. Since September 2020, the Egregor ransomware attack has amassed more than 200 victims, including Crytek and Ubisoft. Fortunately, we haven’t seen much action from the ransomware group since the arrest of some of its members.
What do you think about this? Do tell us your opinions in the comments below!
Thanks! Do share your feedback with us. ⚡
How can we make this post better? Your help would be appreciated. ✍



